Every business handles sensitive documents, yet over 60 percent of companies have experienced at least one security breach affecting their confidential files. Most people think adding a password or two is enough to keep things safe. That barely scratches the surface since the real danger comes from invisible risks lurking inside everyday workflows. Understanding the importance of document security is crucial for protecting these files.
Understanding the importance of document security is vital for every organization. The importance of document security cannot be ignored in our increasingly digital world.
Table of Contents
- What Is Document Security And Its Key Components?
- Why Document Security Matters For Businesses
- How Document Security Protects Sensitive Information
- Real-World Impacts Of Inadequate Document Security
- Future Trends In Document Security Practices
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement multi-layered security protocols | Use encryption, access controls, and authentication to safeguard sensitive data effectively. |
| Prioritize key management practices | Establish protocols for secure generation, distribution, and destruction of encryption keys to maintain data integrity. |
| Adopt a Zero Trust approach | Verify every access request continuously to minimize vulnerabilities and enhance document protection strategies. |
| Utilize AI for threat detection | Employ machine learning to identify unusual access patterns and predict potential security breaches proactively. |
| Develop comprehensive training programs | Educate employees on document handling best practices to prevent unintentional data exposure and security mishaps. |
What is Document Security and Its Key Components?
Document security represents a comprehensive strategy designed to protect sensitive information from unauthorized access, modification, or destruction. At its core, document security encompasses a range of technological and procedural safeguards that preserve the confidentiality, integrity, and availability of critical organizational data. Understanding the importance of document security is essential in today’s digital landscape.
Understanding Document Security Fundamentals
Document security goes beyond simple password protection. Research from the National Institute of Standards and Technology (NIST) indicates that comprehensive document security involves multiple layers of protection. These layers include:
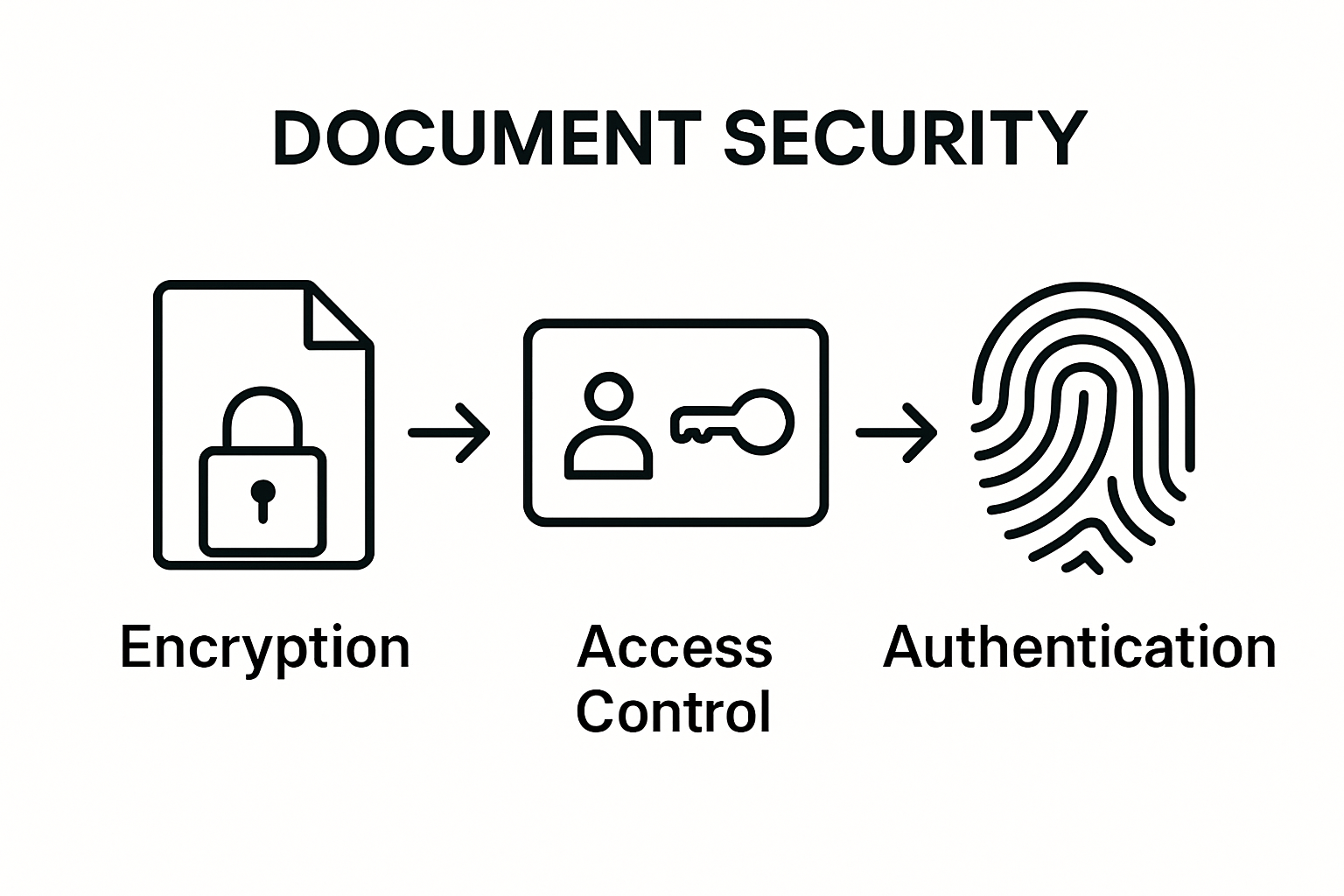
- Encryption technologies that scramble data
- Access control mechanisms
- Authentication protocols
- Secure storage and transmission methods
The primary objectives of document security include preventing data breaches, protecting intellectual property, ensuring regulatory compliance, and maintaining the confidential nature of sensitive information.
Key Components of Robust Document Security
Effective document security relies on several critical components. Public Key Infrastructure (PKI) plays a pivotal role in securing electronic transactions. PKI utilizes asymmetric cryptography, where different keys are used for encryption and decryption, providing a sophisticated method of protecting digital documents.
Key management is another crucial aspect. According to cybersecurity experts at Carnegie Mellon University, proper key management involves generating, distributing, storing, and eventually destroying cryptographic keys to maintain system integrity. Organizations must implement strict protocols that govern how cryptographic keys are created, used, and retired.
Additionally, document security requires a multifaceted approach that combines technological solutions with organizational policies. This includes implementing secure document handling procedures, training employees on best practices, and continuously monitoring and updating security protocols to address emerging digital threats.
By understanding and implementing comprehensive document security strategies, organizations can significantly reduce their vulnerability to data breaches, protect sensitive information, and maintain the trust of their stakeholders. The importance of document security cannot be overstated in this context.
The following table summarizes the key components of robust document security and their purposes, helping readers understand the roles each element plays in protecting sensitive information.
| Component | Purpose |
|---|---|
| Encryption Technologies | Convert data into unreadable format to prevent unauthorized access |
| Access Control Mechanisms | Restrict who can view, modify, or share documents |
| Authentication Protocols | Verify user identities before granting access |
| Secure Storage/Transmission | Ensure documents remain protected during storage and transfer |
| Public Key Infrastructure (PKI) | Secure electronic transactions using asymmetric cryptography |
| Key Management | Manage the lifecycle of cryptographic keys for data integrity |
| Secure Document Handling Policies | Define trusted processes and employee roles for document use |
Why Document Security Matters for Businesses
Document security is not merely a technical requirement but a critical business imperative that directly impacts organizational survival and reputation. In an era of increasing digital threats, businesses must recognize the profound implications of robust document protection strategies.
Financial and Reputational Risks of Poor Document Security
Research from the Organisation for Economic Co-operation and Development reveals that information security breaches can result in substantial economic consequences. The potential risks include:
- Direct financial losses from data theft
- Regulatory compliance penalties
- Permanent damage to brand reputation
- Loss of customer trust and potential market share
Cybercriminals target business documents because they contain valuable intellectual property, financial records, strategic plans, and sensitive customer information. A single security breach can potentially devastate an organization’s competitive positioning and long-term viability.
In discussing the importance of document security, organizations must prioritize securing sensitive information to avoid costly breaches.
Strategic Importance of Comprehensive Document Protection
Beyond immediate financial concerns, document security represents a strategic business capability. Companies that demonstrate strong information protection practices differentiate themselves in competitive markets. Learn more about advanced document protection strategies on our blog.
Effective document security involves more than technological solutions. It requires a holistic approach integrating technological tools, employee training, and organizational policies. Businesses must develop comprehensive frameworks that:
- Identify sensitive information categories
- Implement multi-layered security protocols
- Create clear guidelines for document handling
- Establish continuous monitoring and assessment mechanisms
By prioritizing document security, organizations protect their most valuable assets digital information transforming potential vulnerabilities into strategic advantages. The investment in robust document protection is not an expense but a critical foundation for sustainable business success in the digital age.
How Document Security Protects Sensitive Information
Document security serves as a critical shield protecting an organization’s most valuable digital assets from potential threats and unauthorized access. By implementing sophisticated protection mechanisms, businesses can safeguard confidential information across various digital and physical environments.
Layers of Information Protection
Research from SUNY Geneseo highlights the multifaceted approach required to secure sensitive documents. Comprehensive protection involves multiple strategic layers that work together to prevent unauthorized access and potential data breaches:
- Encryption technologies that transform readable data into unreadable code
- Access control systems that restrict document visibility
- Authentication protocols verifying user identities
- Secure transmission channels preventing data interception
These interconnected protection layers create a robust defense mechanism that adapts to evolving digital security challenges.
Advanced Protection Mechanisms
Digital rights management (DRM) represents a sophisticated approach to document security. This technology allows organizations to control precisely how documents can be accessed, shared, and manipulated. Key features include:
- Restricting document printing
- Preventing copy and paste functions
- Setting automatic document expiration
- Tracking document usage and interactions
The importance of document security extends to all levels of an organization, influencing trust among clients and stakeholders.
By implementing granular control mechanisms, organizations can ensure that sensitive information remains protected throughout its lifecycle, reducing the risk of unauthorized distribution or misuse.
Moreover, document security extends beyond technological solutions. Check out our guide on advanced document protection strategies to understand how comprehensive security requires a holistic approach combining technology, policy, and human awareness.
Organizations that understand the importance of document security are better positioned to mitigate risks effectively.
Document security is fundamentally about understanding the importance of document security to protect against threats.
Effective document security is not about creating impenetrable barriers but developing intelligent, adaptive protection strategies that balance accessibility with rigorous safeguarding protocols.
Knowledge of the importance of document security can significantly lower risks associated with data handling.
 Organizations must continuously evolve their approach, recognizing that protecting sensitive information is an ongoing process requiring vigilance, technological innovation, and strategic planning.
Organizations must continuously evolve their approach, recognizing that protecting sensitive information is an ongoing process requiring vigilance, technological innovation, and strategic planning.
Real-World Impacts of Inadequate Document Security
Document security breaches extend far beyond theoretical risks, presenting tangible and often devastating consequences for organizations across various sectors. Understanding these real-world impacts illuminates the critical need for comprehensive document protection strategies.
Financial and Operational Consequences
Research from the U.S. Government Accountability Office demonstrates the escalating nature of information security incidents, revealing the profound vulnerabilities organizations face. The financial ramifications of inadequate document security can be catastrophic:
- Direct monetary losses from data theft and recovery efforts
- Significant expenses associated with breach investigations
- Potential legal penalties and regulatory compliance fines
- Long-term revenue reduction due to reputational damage
Operational disruptions frequently accompany document security failures. When sensitive information is compromised, organizations may experience complete system shutdowns, critical data loss, and extended recovery periods that can paralyze business functions.
Reputational and Trust Erosion
Understanding the importance of document security is essential for protecting customer relationships.
Perhaps the most insidious impact of document security breaches is the irreparable damage to organizational reputation. Customer and stakeholder trust becomes severely compromised when sensitive information is exposed. The consequences include:
Additionally, the importance of document security is emphasized in corporate governance frameworks.
- Immediate loss of customer confidence
- Negative media coverage
- Potential long-term brand reputation destruction
- Difficulty attracting new clients or business partners
Explore our comprehensive guide on protecting your organization’s digital assets to understand how proactive document security can mitigate these risks.
Beyond immediate financial and reputational consequences, document security breaches can trigger cascading effects that threaten an organization’s entire ecosystem. Small vulnerabilities can quickly escalate into systemic risks, potentially compromising not just individual documents but entire organizational infrastructures.
This table outlines the main financial and reputational consequences faced by organizations as a result of inadequate document security, highlighting why proactive protection is essential.
| Type of Impact | Description |
|---|---|
| Direct Monetary Losses | Immediate financial losses due to data theft and efforts to recover data |
| Regulatory Penalties | Fines and sanctions for failing to comply with data protection regulations |
| Operational Disruption | Downtime and halted business operations during recovery |
| Reputational Damage | Loss of customer trust, negative publicity, and long-term harm to brand image |
| Loss of Market Share | Reduced competitiveness as customers seek trustworthy alternatives |
In the digital age, document security is not an optional enhancement but a fundamental business survival strategy. Organizations must recognize that protecting sensitive information is a continuous, dynamic process requiring constant vigilance, technological adaptation, and strategic foresight.
Understanding the importance of document security contributes to better compliance with regulations.
Future Trends in Document Security Practices
The landscape of document security is rapidly evolving, driven by technological advancements, increasing cyber threats, and the need for more sophisticated protection mechanisms. Organizations must stay ahead of emerging trends to effectively safeguard their sensitive information.
Zero Trust Architecture: A Paradigm Shift
Research exploring the Zero Trust cybersecurity framework highlights a transformative approach to document security. Zero Trust Architecture (ZTA) represents a fundamental reimagining of traditional security models, moving beyond perimeter-based defenses to a more dynamic and granular protection strategy:
- Continuous authentication for every access request
- Least privilege access principles
- Granular permission controls
- Real-time verification of user identities
This approach assumes no inherent trust, requiring verification at every stage of document access and interaction. Organizations can significantly reduce vulnerability by implementing these rigorous authentication mechanisms.
Artificial Intelligence and Advanced Protection
Artificial intelligence is revolutionizing document security by introducing unprecedented levels of intelligent threat detection and prevention. Machine learning algorithms can now:
- Identify unusual access patterns
- Predict potential security breaches
Learn more about our advanced document protection insights from our expert contributors to understand how AI is transforming document security landscape.
Advanced intrusion detection systems powered by AI can analyze massive amounts of data, identifying subtle anomalies that traditional security methods might miss. These intelligent systems provide proactive protection, adapting in real-time to emerging threats and reducing the potential for unauthorized document access.
The future of document security is not about building higher walls, but creating smarter, more adaptive protection ecosystems. Organizations must embrace these emerging technologies, recognizing that document security is a continuous journey of innovation, vigilance, and strategic technological integration.
Ready to Take Control of Your Document Security?
Are you concerned about the risk of unauthorized access, data breaches, or lost productivity in your organization? In “Understanding the Importance of Document Security,” you learned how layered controls and technologies are vital for protecting sensitive documents and maintaining stakeholder trust. Modern threats demand proactive, smart solutions and your business deserves tools designed for serious digital preservation. Explore our Digital Preservation resources and discover strategies for safeguarding critical files today.
Mapsoft.com is built for organizations that prioritize robust document security, workflow efficiency, and compliance. Harness advanced features for PDF protection, automation, and integrity through powerful plug-ins and web-based platforms. Do not wait until vulnerabilities affect your bottom line. Visit Mapsoft.com now and build a secure digital future for your business. Need tailored advice or enterprise-grade support? Reach out for personalized solutions that align with your most pressing security goals.
Frequently Asked Questions
What is document security?
Document security is a comprehensive strategy aimed at protecting sensitive information from unauthorized access, modification, or destruction. It involves various technological and procedural safeguards to ensure the confidentiality, integrity, and availability of organizational data.
Why is document security important for businesses?
Document security is crucial for businesses as it prevents data breaches, protects intellectual property, ensures regulatory compliance, and maintains the trust of stakeholders. Security failures can lead to financial losses, reputational damage, and erosion of customer trust.
What are the key components of document security?
Key components of document security include encryption technologies, access control mechanisms, authentication protocols, and secure storage and transmission methods. Together, these elements provide multiple layers of protection against unauthorized access and data breaches.
How can organizations implement effective document security measures?
Organizations can implement effective document security measures by adopting a multi-layered approach that includes identifying sensitive information, establishing strict access controls, using encryption, training employees on security best practices, and continuously monitoring and updating security protocols.
Recommended
- Blog –
- Michael Peters –
- Digital Preservation –
- The Role of Notary Public Seals and Stamps in Documentation – My Mobile Notary
- Secure Your Documents With Local Notary Services – My Mobile Notary
Summary
Inadequate understanding of the importance of document security can lead to severe repercussions for businesses.
Understanding the importance of document security empowers organizations to foster a culture of proactive protection.
Ultimately, the importance of document security is evident in every aspect of managing sensitive information.
It is essential for leaders to recognize the importance of document security in their strategic planning.
The importance of document security is not just a compliance requirement, but a strategic advantage.
Understanding the importance of document security enhances organizational resilience against cyber threats.
Organizations must keep the importance of document security at the forefront of their operations.
Awareness of the importance of document security can drive innovation in information protection.
Thus, the importance of document security is a topic that should be addressed regularly in training sessions.
By prioritizing the importance of document security, businesses can foster a culture of trust and integrity.



