Companies are often caught in a tug of war between keeping digital systems safe and making sure people can use them easily. You might expect security experts to always prioritize strict protection at every turn. Yet studies show that overly complicated security controls can actually drive users to create risky workarounds, making systems less secure overall. This surprising contradiction reshapes the way organizations design both their workflows and defenses.
Table of Contents
- What Is Balancing Security And Usability?
- Why Is Balancing Security And Usability Important For Businesses?
- Key Concepts In Balancing Security And Usability
- Real-World Implications Of Security And Usability Trade-offs
- Best Practices For Achieving Balance In Document Workflows
Quick Summary
| Takeaway | Explanation |
|---|---|
| Prioritize usability in security measures | Security protocols should facilitate user efficiency and not hinder workflows. |
| Implement risk-based authentication | Adjust security measures based on specific user contexts and behavior to reduce friction. |
| Focus on user-centric design principles | Create intuitive security interfaces that require minimal user effort and promote understanding. |
| Educate and train users continuously | Regular training ensures users remain compliant and aware of evolving security protocols. |
| Balance security and operational efficiency | Effective security should enhance productivity without sacrificing user experience or access. |
What is Balancing Security and Usability?
Balancing security and usability represents a critical challenge for organizations managing digital systems and workflows. This concept describes the strategic effort to protect digital assets and user experiences simultaneously, ensuring robust protection without compromising user efficiency or engagement.
The Core Conflict Between Security and User Experience
At its fundamental level, balancing security and usability involves managing two seemingly opposing objectives. Security measures aim to restrict and protect, while usability focuses on creating smooth, intuitive interactions.
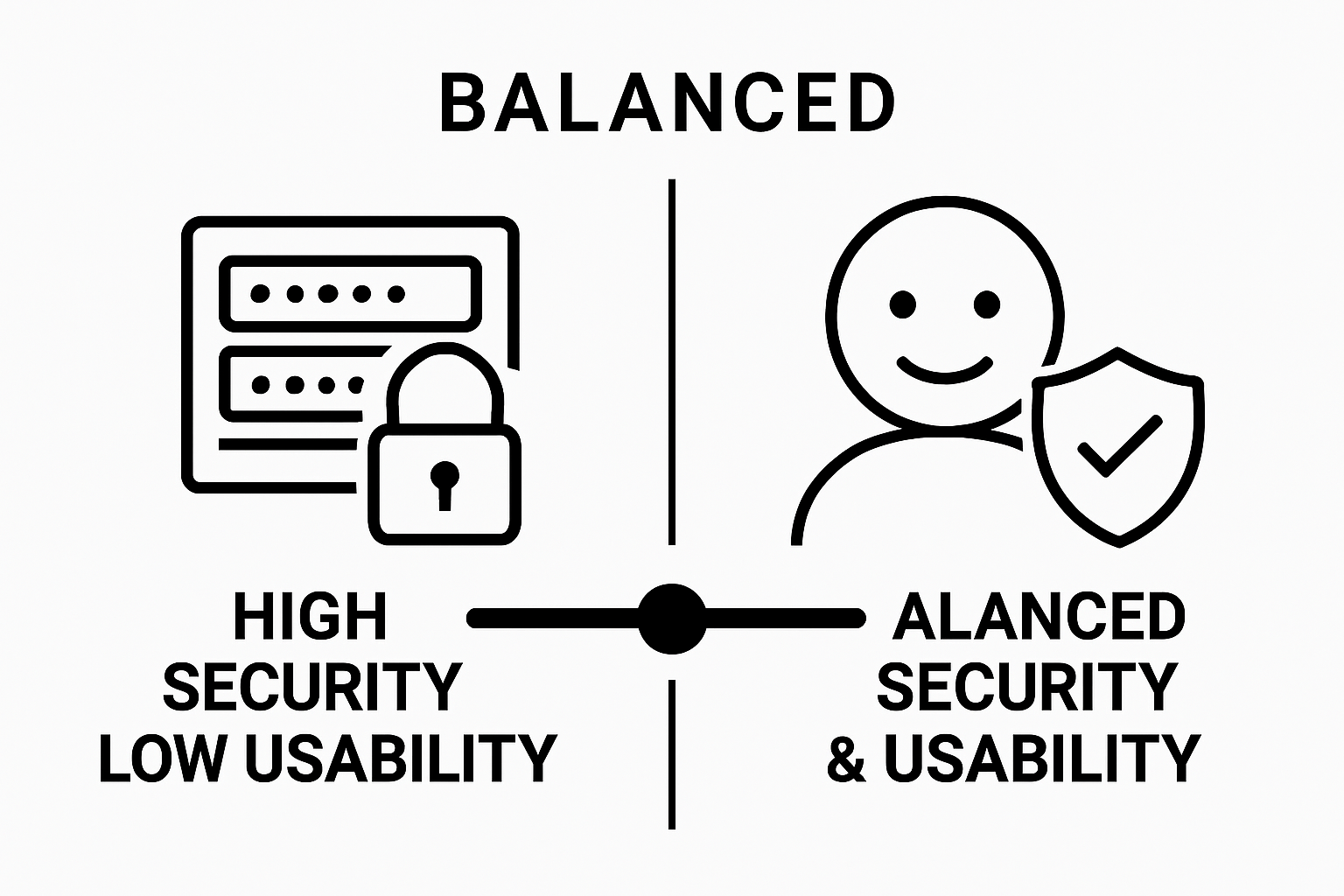 Research from IEEE highlights that these goals are often perceived as mutually exclusive, creating a complex design challenge for system architects and developers.
Research from IEEE highlights that these goals are often perceived as mutually exclusive, creating a complex design challenge for system architects and developers.
Key aspects of this conflict include:
- Restrictive Security Controls: Extensive authentication processes that slow user interactions
- User Convenience: Desire for quick, frictionless system access
- Risk Management: Protecting sensitive information while maintaining workflow efficiency
Understanding the Strategic Trade-offs
Successful balancing requires thoughtful design strategies that recognize human behavior patterns. According to NIST Special Publication, system designers must consider how users might develop unsafe workarounds if security measures become too cumbersome.
Effective approaches involve:
- Contextual Security: Implementing protection mechanisms that adapt to specific user roles
- Intelligent Authentication: Using risk-based verification methods
- User-Centric Design: Creating security protocols that feel natural and integrated
Ultimately, balancing security and usability is not about achieving perfect equilibrium, but creating adaptive systems that dynamically respond to evolving technological landscapes and user expectations.
Why is Balancing Security and Usability Important for Businesses?
Businesses today operate in a complex digital ecosystem where security and user experience are critical determinants of organizational success. Balancing these two competing priorities is not just a technical challenge but a strategic imperative that directly impacts productivity, customer satisfaction, and bottom-line performance.
Financial and Operational Impact
The consequences of poor security and usability integration can be significant. NIST research emphasizes that cybersecurity measures must be designed to complement operational effectiveness, not hinder it. Ineffective security protocols can lead to substantial financial risks:
- Productivity Losses: Complex security systems slow down workflow processes
- Employee Frustration: Overly restrictive systems decrease workforce morale
- Customer Abandonment: Difficult user experiences drive potential clients away
Reputation and Trust Management
Moreover, businesses must recognize that security and usability directly influence organizational reputation. According to the National Academies Press, systems that are difficult to use are more prone to user errors, potentially compromising security and eroding stakeholder trust.
Key reputation risks include:
- Data Breach Potential: Circumvented security measures increase vulnerability
- Customer Confidence: Seamless, secure experiences build long-term trust
- Competitive Differentiation: Organizations with robust yet user-friendly systems gain market advantage
Strategic Competitive Advantage
Ultimately, successful businesses view security and usability not as competing objectives, but as complementary strategies. By investing in intelligent design that prioritizes both protection and user experience, organizations can create resilient digital environments that adapt to evolving technological landscapes while maintaining high levels of security and operational efficiency.
Key Concepts in Balancing Security and Usability
Navigating the complex landscape of security and usability requires understanding several fundamental principles that guide effective digital system design. These key concepts provide organizations with a strategic framework for creating robust yet user-friendly technological environments.
Risk-Based Authentication
Risk-based authentication emerges as a critical concept in balancing security and usability.
VIDEO:video_content] [The Open Web Application Security Project (OWASP) explains this approach as a dynamic method of evaluating authentication requirements based on contextual risk factors. Instead of applying uniform security measures, this concept allows systems to adjust protection levels according to specific user behaviors and potential threat indicators.
Key characteristics of risk-based authentication include:
- Contextual Analysis: Evaluating login attempts based on location, device, and user history
- Adaptive Security: Implementing stronger verification for high-risk scenarios
- Reduced User Friction: Minimizing unnecessary authentication steps for low-risk interactions
User-Centric Security Design
User-centric security design represents another pivotal concept that prioritizes human experience within security frameworks. This approach recognizes that complex security protocols often lead users to develop counterproductive workarounds that ultimately compromise system integrity.
Primary principles of user-centric design involve:
- Intuitive Interface: Creating security mechanisms that feel natural and understandable
- Minimal Cognitive Load: Designing authentication processes that require minimal user effort
- Transparent Communication: Clearly explaining security requirements and potential risks
Continuous Adaptive Trust
Continuous adaptive trust represents an advanced concept that goes beyond traditional static security models. This approach views security as a dynamic, ongoing process that continuously reassesses user trustworthiness based on real-time behavioral data and system interactions.
By integrating these key concepts, organizations can develop sophisticated security strategies that protect digital assets without sacrificing user experience, ultimately creating more resilient and user-friendly technological ecosystems.
The table below compares the core concepts discussed in the article for balancing security and usability, providing a concise overview of their distinctive features and organizational benefits.
| Concept | Description | Key Benefits |
|---|---|---|
| Risk-Based Authentication | Security adapts to user roles, behavior, and context | Reduces friction, prioritizes high-risk scenarios |
| User-Centric Security Design | Security protocols designed around intuitive, user-friendly experiences | Minimizes workarounds, increases compliance |
| Continuous Adaptive Trust | Ongoing, real-time assessment of user trustworthiness based on system use | Dynamically responds to emerging threats and behaviors |
Real-World Implications of Security and Usability Trade-offs
The abstract principles of security and usability transform into concrete challenges when applied to actual organizational environments. Understanding these real-world implications reveals the complex dynamics that shape technological interactions and organizational strategies.
Economic and Operational Consequences
Research from the National Academy of Sciences highlights that security and usability trade-offs are not merely technical considerations but have substantial economic ramifications. Organizations face direct financial impacts when their digital systems fail to strike an appropriate balance between protection and accessibility.
Key economic implications include:
- Technology Investment: Substantial resources required to develop adaptive security systems
- Productivity Costs: Inefficient security protocols can significantly reduce operational efficiency
- Talent Retention: Overly restrictive systems can diminish employee satisfaction and engagement
Human Behavior and System Design
The interaction between security mechanisms and human behavior represents a critical real-world consideration. Complex security requirements often trigger unintended user responses, potentially creating more significant vulnerabilities than those they aim to prevent.
Significant behavioral challenges involve:
- Workaround Development: Users creating alternative methods to bypass complex security protocols
- Cognitive Overload: Increased mental strain from navigating intricate authentication processes
- Compliance Fatigue: Diminishing user willingness to adhere to security guidelines
Organizational Risk Management
Effective security and usability integration demands a holistic approach to risk management. Organizations must develop sophisticated strategies that recognize the dynamic nature of technological threats and user expectations.
By acknowledging these real-world implications, businesses can design more intelligent, adaptive systems that protect digital assets without creating unnecessary friction. The goal is not absolute security, but a nuanced approach that balances protection, user experience, and organizational objectives.
This table summarizes economic and operational implications organizations may face due to security and usability trade-offs, providing an at-a-glance understanding of how these factors can impact business outcomes.
| Implication | Description |
|---|---|
| Technology Investment | Significant costs to develop and maintain adaptive security systems |
| Productivity Costs | Inefficient controls can slow down workflows and business operations |
| Talent Retention | Overly restrictive or complex systems reduce employee satisfaction and engagement |
| Customer Abandonment | Challenging user experiences can drive customers to seek more user-friendly alternatives |
| Data Breach Risk | Workarounds or errors increase the likelihood of security incidents |
Best Practices for Achieving Balance in Document Workflows
Achieving an optimal balance between security and usability in document workflows requires strategic planning, sophisticated technological solutions, and a deep understanding of organizational dynamics. Successful implementations demand comprehensive approaches that transcend traditional security paradigms.
Access Control and Authentication Strategies
NIST Special Publication 800-210 provides critical guidance on implementing robust yet user-friendly access management. The fundamental principle involves creating granular, context-aware authentication mechanisms that adapt to specific user roles and document sensitivity levels.
Key authentication best practices include:
- Least Privilege Principle: Granting minimal necessary access rights
- Multi-Factor Authentication: Implementing layered verification processes
- Dynamic Permission Management: Adjusting access rights based on real-time context
Workflow Integration and User Experience
Effective document security requires seamless integration of protective measures within existing workflow structures. ResearchGate studies reveal that successful approaches focus on creating intuitive security mechanisms that feel like natural extensions of user interactions.
Critical workflow integration strategies involve:
- Contextual Security Cues: Providing clear, non-intrusive security indicators
- Adaptive Authentication: Developing intelligent verification processes
- Continuous User Training: Embedding security awareness into daily workflows
Technological and Cultural Alignment
Balancing security and usability transcends technological solutions. Organizations must cultivate a holistic approach that combines advanced technological tools with a culture of security awareness. This requires ongoing education, transparent communication, and a collaborative approach to risk management.
For more insights into document workflow optimization, explore our comprehensive resources that delve deeper into practical implementation strategies. By embracing these best practices, organizations can create resilient document management systems that protect sensitive information without compromising operational efficiency.

Overcome the Security and Usability Challenge in Your Document Workflows
Struggling to find the right balance between ironclad security and seamless usability for your PDF processes? The article highlights the daily frustrations faced by organizations when strict security controls disrupt workflow efficiency or force users into risky workarounds. Building adaptive systems that protect sensitive documents without sacrificing usability is essential, especially with complex requirements like role-based access, risk-based authentication, and dynamic compliance. Mapsoft.com specializes in helping businesses achieve this crucial balance so you can meet efficiency targets while maintaining the document security you need. For strategies around safeguarding essential records, explore our Digital Preservation resource hub.
Ready to boost both security and productivity in your PDF workflows? Start by discovering how the Mapsoft PDF Hub empowers you to manage, secure, and automate documents at scale. Act now to minimize workflow disruptions and protect your digital assets with intelligent tools made for modern enterprises. Visit our main site for tailored solutions and expert support.
Frequently Asked Questions
What is the main challenge in balancing security and usability?
The main challenge lies in managing two opposing objectives: security measures aim to protect and restrict access, while usability focuses on creating smooth, intuitive user interactions.
Why is balancing security and usability crucial for businesses?
Balancing security and usability is crucial because it directly impacts productivity, customer satisfaction, and overall organizational success. Poor integration can lead to operational inefficiencies and financial losses.
How can organizations implement risk-based authentication?
Organizations can implement risk-based authentication by evaluating user behaviors and contextual risk factors, allowing security measures to adapt according to the level of threat or user activity.
What are some best practices for maintaining usability in security protocols?
Best practices include using the least privilege principle, adopting multi-factor authentication, and ensuring seamless integration of security measures within existing workflows to enhance user experience.
Recommended
- Digital Preservation –
- long-term preservation –
- digital preservation –
- Effective Website Design: Key Principles and Proven Strategies 2025
- The ever growing number of security questionnaires and what you and your company can do to face it



