Secure document disposal sounds like overkill for tossing out old papers, but the truth is there is a major difference between just throwing something away and making it disappear for good. Professional shredding can render documents into bits so small they are impossible to reconstruct, and forensic experts warn that basic shredding barely slows down today’s data thieves. Most people think a trash can is enough, yet that simple move can put companies at risk for lawsuits, lost trust, and financial disaster.
Table of Contents
- What Is Secure Document Disposal And Its Purpose?
- Why Secure Document Disposal Is Critical For Businesses
- How Secure Document Disposal Protects Sensitive Information
- Key Concepts In Secure Document Disposal Practices
Quick Summary
| Takeaway | Explanation |
|---|---|
| Secure document disposal is essential. | It permanently destroys sensitive information, preventing unauthorized access and misuse. |
| Categorize documents by sensitivity. | Not all documents require the same destruction methods; assess confidentiality and risks accordingly. |
| Implement robust disposal methods. | Use specialized shredding and software techniques to ensure data cannot be reconstructed or recovered. |
| Understand legal compliance requirements. | Businesses must follow regulations to protect sensitive information and avoid legal penalties. |
| Adopt a holistic approach to document security. | Integrate destruction protocols with organizational policies for comprehensive information governance. |
What is Secure Document Disposal and Its Purpose?
Secure document disposal represents a critical process of systematically destroying sensitive information to prevent unauthorized access or potential data misuse. Unlike standard trash disposal, secure document disposal involves deliberate methods designed to permanently render documents unreadable and irretrievable.
Understanding Document Sensitivity
Not all documents require the same level of destruction. Organizations must categorize documents based on their confidentiality and potential risk. Documents containing personal identifiable information, financial records, medical histories, or corporate strategies demand meticulous disposal techniques.
The table below organizes common categories of sensitive documents and provides examples to clarify what kinds of information require secure disposal.
| Document Category | Examples |
|---|---|
| Personal Identification Records | Social security documents, passports, birth certificates |
| Financial Documentation | Bank statements, tax returns, investment portfolios |
| Corporate Information | Strategic plans, employee records, confidential contracts |
| Medical Files | Patient histories, insurance documents, treatment records |
Key categories of sensitive documents include:
- Personal Identification Records: Social security documents, passports, birth certificates
- Financial Documentation: Bank statements, tax returns, investment portfolios
- Corporate Information: Strategic plans, employee records, confidential contracts
- Medical Files: Patient histories, insurance documents, treatment records
Comprehensive Disposal Methodologies
Secure document disposal encompasses multiple destruction strategies tailored to different media types. According to Harvard University’s Information Security Policy, information designated as sensitive must be rendered completely unreadable through specific techniques.
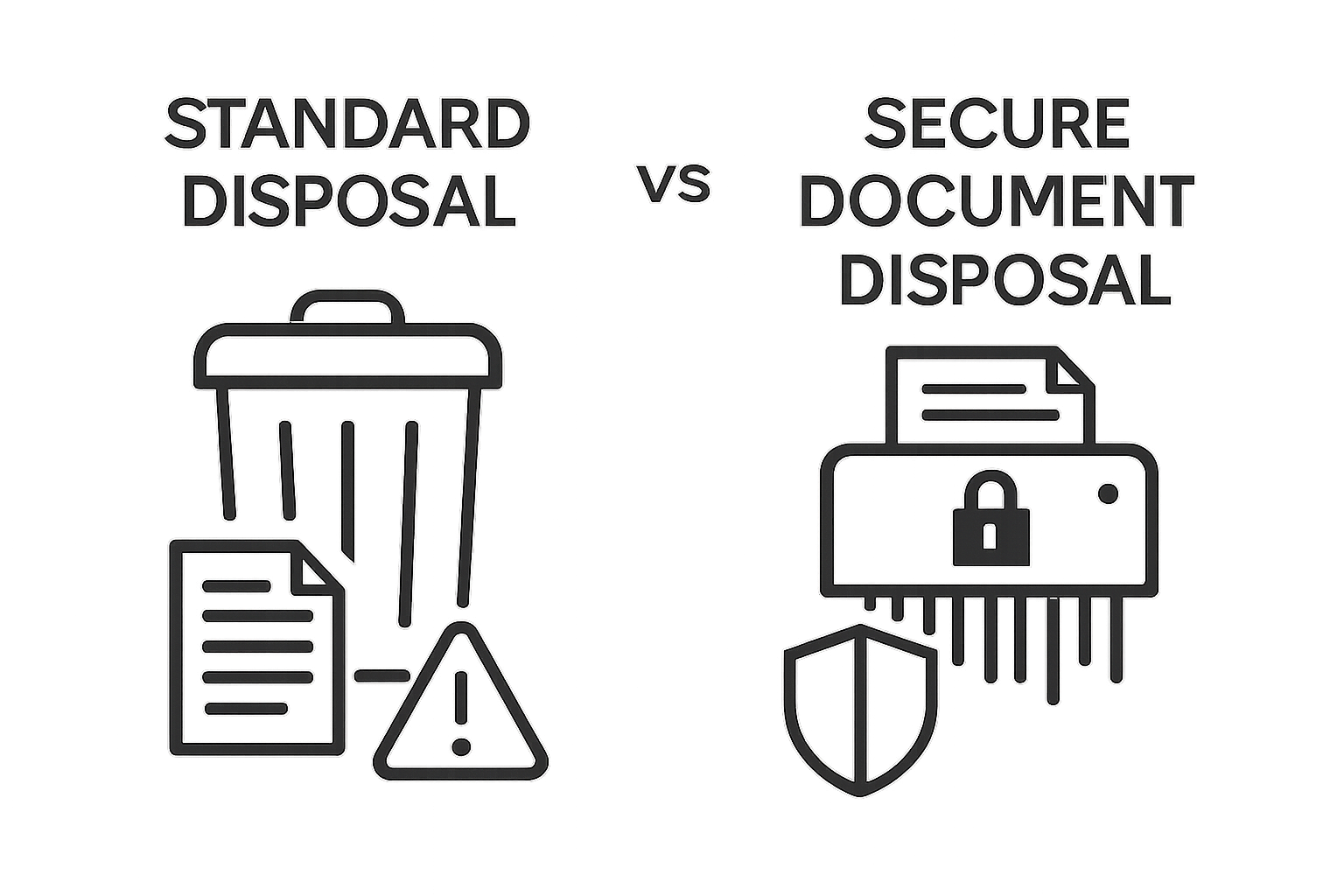
For physical documents, this typically involves professional shredding that goes beyond standard strip cutting. Cross-cut or micro-cut shredders pulverize paper into tiny, unrecognizable fragments, making reconstruction virtually impossible. Digital documents require specialized software that securely erases data, overwriting file storage sectors to eliminate any potential data recovery.
The fundamental purpose of secure document disposal extends beyond simple waste management. It serves as a critical defense mechanism against identity theft, corporate espionage, compliance violations, and potential legal vulnerabilities.
By implementing robust disposal protocols, organizations protect sensitive information, maintain professional integrity, and safeguard individual and institutional privacy.
Why Secure Document Disposal is Critical for Businesses
Businesses face unprecedented risks from improperly managed sensitive information. Secure document disposal has become a fundamental strategy for protecting organizational integrity, financial stability, and legal compliance in an increasingly complex digital landscape.
This table summarizes key regulatory and organizational reasons why businesses need secure document disposal, emphasizing the importance for different aspects of operations.
| Compliance and Risk Area | Description |
|---|---|
| Legal Compliance | Required by regulations to protect consumer and client data |
| Financial Risk | Prevents losses from lawsuits, fines, and breaches |
| Reputation Management | Maintains customer trust and professional integrity |
| Client Confidentiality | Safeguards sensitive business and personal information |
Legal and Regulatory Compliance Imperatives
Government regulations mandate strict protocols for handling confidential information. According to the Federal Trade Commission, businesses must implement robust disposal mechanisms to protect consumer data and prevent potential legal consequences.
Key regulatory compliance requirements include:
- Protecting personally identifiable information
- Maintaining client confidentiality standards
- Preventing unauthorized data access
- Demonstrating responsible information management
Financial and Reputational Risk Management
The consequences of inadequate document disposal extend far beyond immediate legal penalties. Data breaches can result in substantial financial losses, including potential lawsuits, regulatory fines, and irreparable damage to organizational reputation. Companies that fail to protect sensitive information risk losing customer trust and facing significant financial repercussions.
Moreover, industries such as healthcare, finance, and legal services are particularly vulnerable. Confidential client records, financial statements, strategic plans, and personal information require meticulous destruction to prevent potential corporate espionage or identity theft. Learn more about our comprehensive document security solutions to understand how businesses can effectively mitigate these risks.
Effective secure document disposal is not merely a technical requirement but a strategic imperative. By implementing comprehensive destruction protocols, businesses demonstrate their commitment to data protection, ethical practices, and professional responsibility. This approach safeguards not just information, but the fundamental trust that underpins successful business relationships.
How Secure Document Disposal Protects Sensitive Information
Secure document disposal represents a sophisticated defense mechanism designed to shield organizations and individuals from potential data vulnerabilities. By implementing strategic destruction protocols, sensitive information becomes permanently inaccessible, preventing unauthorized reconstruction or misuse.
Information Vulnerability and Data Reconstruction
Modern data recovery technologies can reconstruct seemingly destroyed documents through advanced forensic techniques. According to National Institute of Standards and Technology, traditional disposal methods like simple paper shredding or basic digital deletion are insufficient to guarantee complete information protection.
Potential risks of inadequate document disposal include:
- Partial document reconstruction from fragmented materials
- Digital data recovery from improperly wiped storage devices
- Unauthorized access to discarded physical documents
- Potential identity theft and corporate espionage
Multi-Layered Destruction Strategies
Comprehensive document disposal requires multi-dimensional approaches tailored to different information types. Physical documents demand cross-cut or micro-cut shredding that reduces paper to microscopic fragments, while digital files require specialized overwriting techniques that permanently eliminate data traces.
Digital information protection involves:
- Complete sector overwriting on storage devices
- Cryptographic erasure techniques
- Degaussing magnetic media
- Physical destruction of storage hardware
Professional secure document disposal goes beyond simple destruction. It represents a systematic approach to information management, ensuring that sensitive data becomes irretrievable across physical and digital domains. By implementing rigorous disposal protocols, organizations create an essential protective barrier against potential security breaches, maintaining confidentiality and preserving institutional integrity.
The following table compares physical and digital secure document disposal methods, outlining the destruction approach and what each method protects against.
| Document Type | Disposal Method | Primary Protection Provided |
|---|---|---|
| Physical Documents | Cross-cut/micro-cut shredding | Prevents paper reconstruction, identity theft |
| Hard Drives | Degaussing, physical destruction | Stops digital recovery, ensures full erasure |
| Magnetic Tapes | Magnetic erasure | Eliminates retrievable stored data |
| Solid State Drives | Cryptographic wiping | Destroys digital traces, ensures data loss |
| Cloud Storage | Secure data overwriting | Prevents file recovery from remote servers |
Key Concepts in Secure Document Disposal Practices
Secure document disposal is a complex discipline requiring strategic understanding beyond simple destruction. Organizations must develop comprehensive approaches that address the nuanced challenges of protecting sensitive information across physical and digital domains.
Information Classification and Risk Assessment
Effective document disposal begins with meticulous information classification. Not all documents carry equal sensitivity, and understanding the risk profile becomes crucial for implementing appropriate destruction protocols. Indiana University’s data management guidelines emphasize the importance of evaluating document risk before determining disposal methods.
Key classification criteria include:
- Confidentiality level of information
- Potential financial impact of data exposure
- Regulatory compliance requirements
- Potential legal and reputational consequences
Destruction Methodology Selection
Document disposal strategies must be tailored to specific media types and information sensitivity. Physical documents require different destruction techniques compared to digital storage, demanding specialized approaches that guarantee complete information elimination.
Destruction methods vary across different information formats:
- Paper Documents: Cross-cut shredding
- Hard Drives: Degaussing and physical destruction
- Magnetic Tapes: Magnetic erasure
- Solid State Drives: Cryptographic wiping
- Cloud Storage: Secure data overwriting
Professional secure document disposal transcends technical processes. It represents a holistic approach to information governance, integrating technological solutions with organizational policies and risk management strategies. By understanding and implementing comprehensive disposal practices, businesses can effectively protect their most valuable asset: confidential information.

Take Control of Secure Document Disposal With Mapsoft Solutions
Worried about the risks of improper document disposal? As highlighted in this article, failing to fully secure your sensitive data can lead to identity theft, financial loss, and costly compliance breaches. You work hard to classify and destroy confidential information, but without the right digital tools, data hiding in your PDF workflows can still be vulnerable. Protecting your business requires more than just a good shredding policy—it calls for true digital preservation and airtight control over every document lifecycle stage. See how our Digital Preservation solutions can help.
Take action now to prevent data breaches before they happen. Mapsoft’s advanced range of PDF tools offers seamless document sanitization, secure redaction, and automated batch processing for even the most complex workflows. Visit Mapsoft.com to discover how our expertise with Adobe® and custom solutions can transform your approach to secure document disposal. Make the switch to truly secure document management today.
Frequently Asked Questions
What is secure document disposal?
Secure document disposal is the process of systematically destroying sensitive information to prevent unauthorized access. It involves methods like professional shredding and data erasure, ensuring that documents are rendered unreadable and irretrievable.
Why is secure document disposal important for businesses?
Secure document disposal is vital for businesses to protect sensitive information from identity theft, corporate espionage, and legal compliance violations. It helps to maintain customer trust, financial stability, and organizational integrity.
What types of documents require secure disposal?
Documents that require secure disposal include personal identification records, financial documentation, corporate information, and medical files. These documents contain sensitive information that, if mishandled, could lead to significant legal and financial repercussions.
What methods are used for secure document disposal?
Secure document disposal utilizes various methods including cross-cut and micro-cut shredding for physical documents, and specialized software for digital files. Digital disposal techniques may include complete sector overwriting, cryptographic erasure, and physical destruction of storage devices.
Recommended
- Understanding the Importance of Document Security –
- What is PDF Redaction? Completely Understanding Its Importance
- Why Use PDF Format for Your Business Success
- Unlock PDF Compare: 7 Ways to Enhance Your Workflow
- The Role of Notary Public Seals and Stamps in Documentation – My Mobile Notary
- Office Furniture Dismantling Guide 2025: Trusted UK Solutions | Schott Removals



