Sensitive documents exchanged between partners in United States, Canada, and across Europe often carry hidden security risks that few IT managers can ignore. PDF files have evolved into more than just digital paperwork, becoming a primary target for sophisticated attacks that threaten both regulatory compliance and organizational trust. By understanding the most common PDF security risks and how advanced Adobe solutions tackle these vulnerabilities, enterprise leaders can better protect vital information and maintain stronger digital defenses.
Table of Contents
- Defining Common PDF Security Risks
- Major Types of PDF Vulnerabilities
- How Attackers Exploit PDF Weaknesses
- Impact on Enterprise Security and Compliance
- Prevention Tactics and Mitigation Strategies
- Advanced Solutions for Enterprise PDF Security
Key Takeaways
| Point | Details |
|---|---|
| Understanding PDF Vulnerabilities | Organizations must recognize the multifaceted security risks associated with PDFs, including unauthorized access, data leakage, and malicious code embedding. |
| Implementation of Security Measures | Proactive risk management strategies, including regular updates and vulnerability assessments, are essential to mitigate potential PDF-based cybersecurity threats. |
| Holistic Approach to Security | Enterprises should adopt a comprehensive security strategy that combines technological solutions, employee training, and continuous monitoring for effective PDF document protection. |
| Dynamic Threat Landscape | Cybersecurity threats related to PDFs are evolving, requiring organizations to stay informed and adaptable to continuously emerging vulnerabilities. |
Defining Common PDF Security Risks
PDF documents have become critical vectors for potential cybersecurity vulnerabilities, representing significant risks for organizations handling sensitive information. Understanding document security risks760387_EN.pdf) requires comprehensive insight into the multifaceted threats embedded within digital document formats.
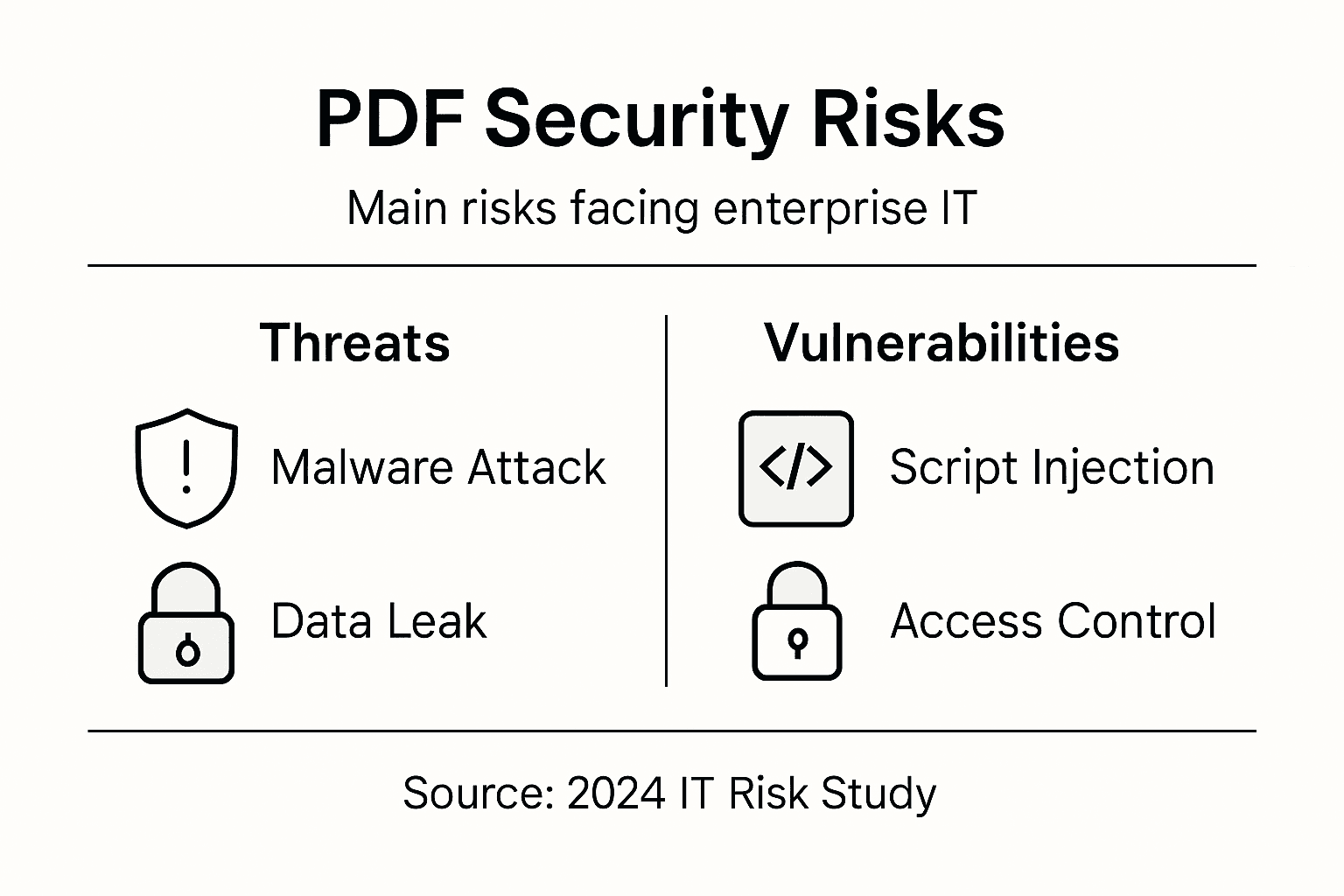
The primary PDF security risks can be categorized into several critical domains:
- Unauthorized Access: Vulnerabilities that allow unauthorized personnel to view, modify, or extract confidential information
- Malicious Code Embedding: Potential for attackers to hide executable scripts or malware within PDF file structures
- Data Leakage: Risks associated with unintentional information disclosure through metadata or hidden document elements
- Injection Attacks: Exploiting PDF reader software vulnerabilities to compromise system integrity
Modern cybersecurity research indicates that PDFs are not merely static documents but complex digital objects with multiple potential attack surfaces. Cyber security researchers emphasize that these risks extend beyond simple document tampering, encompassing sophisticated techniques that can compromise entire organizational networks.
IT managers must recognize that PDF security is not a static concern but a dynamic challenge requiring continuous monitoring and adaptive strategies. The landscape of digital document threats evolves rapidly, demanding proactive risk management approaches that anticipate emerging vulnerabilities.
Pro tip: Implement comprehensive PDF security protocols that include regular vulnerability assessments, strict access controls, and advanced encryption techniques to mitigate potential document-based cybersecurity risks.
Major Types of PDF Vulnerabilities
PDF documents represent a critical attack surface for cybercriminals, with multiple sophisticated vulnerability types that can compromise organizational security. Major cybersecurity vulnerabilities continue to evolve, presenting complex challenges for IT security professionals.
The primary categories of PDF vulnerabilities include:
- Script Injection: Malicious JavaScript embedded within PDF files that can execute unauthorized code
- Use-After-Free Errors: Memory management vulnerabilities allowing attackers to manipulate application behavior
- Buffer Overflow Attacks: Techniques that overwrite memory boundaries to execute arbitrary commands
- Privilege Escalation: Exploits that enable unauthorized users to gain elevated system access
- Metadata Exposure: Unintentional information leakage through document properties and hidden elements
European cybersecurity researchers emphasize that these vulnerabilities are not static threats but dynamic risks constantly adapting to new technological environments. Modern PDF attacks often leverage complex combinations of these vulnerability types, making traditional defense mechanisms increasingly challenging to implement.
The most dangerous PDF vulnerabilities typically exploit weaknesses in PDF reader software, allowing attackers to compromise systems through seemingly innocuous document files. These attacks can range from simple information theft to complete network infiltration, underscoring the critical need for comprehensive security strategies.

The following table summarizes business impacts of each major PDF vulnerability type:
| Vulnerability Type | Typical Attack Vector | Potential Business Impact |
|---|---|---|
| Script Injection | Malicious embedded JavaScript | Credential theft or data compromise |
| Use-After-Free Errors | Exploited memory management | Application crashes or unauthorized access |
| Buffer Overflow Attacks | Out-of-bounds memory writes | System compromise or malware delivery |
| Privilege Escalation | Abused permissions | Unauthorized confidential access |
| Metadata Exposure | Document property leaks | Sensitive data unintentionally shared |
Pro tip: Regularly update PDF reader software, implement advanced content scanning tools, and enforce strict document handling protocols to mitigate the risk of PDF-based security breaches.
How Attackers Exploit PDF Weaknesses
PDF files have become sophisticated vectors for cyberattacks, with threat actors developing increasingly complex methods to exploit document vulnerabilities. Malicious PDF exploitation techniques represent a critical threat landscape that requires comprehensive understanding and proactive defense strategies.
Attackers typically leverage multiple sophisticated approaches to compromise PDF security:
- Social Engineering: Tricking users into opening seemingly legitimate documents
- JavaScript Payload Embedding: Inserting malicious scripts within PDF file structures
- Code Obfuscation: Hiding harmful instructions to bypass traditional security detection
- Zero-Day Exploit Targeting: Identifying and exploiting unknown software vulnerabilities
- Metadata Manipulation: Extracting sensitive information through hidden document properties
Cybersecurity threat researchers highlight that modern PDF attacks are not just about direct malware delivery but involve complex multi-stage infiltration strategies. Attackers frequently combine technical exploitation with psychological manipulation, making these attacks particularly dangerous for unsuspecting users.
The most advanced PDF-based attacks often involve chained vulnerabilities that progressively compromise system integrity. By exploiting weaknesses in PDF reader software, attackers can potentially gain initial access, escalate privileges, and establish persistent network footholds without immediate detection.
Pro tip: Implement rigorous PDF content sanitization processes, use advanced PDF reader security settings, and conduct regular employee training to recognize and prevent sophisticated document-based attack vectors.
Impact on Enterprise Security and Compliance
Enterprise security extends far beyond traditional protection measures, with PDF documents representing a critical vulnerability point that demands comprehensive risk management strategies. Federal research security guidelines emphasize the critical importance of robust document security protocols in maintaining organizational integrity.
The primary compliance challenges related to PDF security include:
- Regulatory Alignment: Meeting stringent requirements from GDPR, HIPAA, and ISO standards
- Data Protection: Preventing unauthorized access and potential information leakage
- Audit Trail Management: Maintaining comprehensive documentation of document interactions
- Risk Mitigation: Identifying and neutralizing potential security vulnerabilities
- Incident Response: Developing rapid containment strategies for potential breaches
Global compliance frameworks underscore the complex landscape of enterprise security, highlighting that PDF vulnerabilities can trigger significant legal and financial repercussions. Non-compliance risks extend beyond immediate financial penalties, potentially damaging organizational reputation and compromising long-term business relationships.
Modern enterprises must adopt a holistic approach to PDF security, integrating technical controls, employee training, and continuous monitoring. The interconnected nature of digital documents means that a single overlooked vulnerability can create cascading security risks across entire organizational ecosystems.
Pro tip: Develop a comprehensive PDF security policy that combines technological solutions, regular employee training, and stringent access control mechanisms to proactively address potential compliance and security challenges.
Prevention Tactics and Mitigation Strategies
Effective PDF security requires a multifaceted approach that combines technological solutions, human awareness, and proactive risk management. Advanced cybersecurity mitigation strategies emphasize the critical importance of comprehensive defense mechanisms that address both technical and human factors.
Key prevention tactics for PDF security include:
- Software Vulnerability Management: Implementing regular patch management and version updates
- Advanced Malware Detection: Using machine learning and behavioral analysis techniques
- Access Control Protocols: Restricting PDF access based on user roles and permissions
- Dynamic Content Scanning: Analyzing PDF files in real-time for potential threats
- Endpoint Protection: Deploying comprehensive security solutions across all device types
Cybersecurity risk mitigation frameworks recommend a layered defense strategy that integrates technical controls with organizational policies. This approach ensures that security measures are not just technologically robust but also aligned with broader enterprise risk management objectives.
Modern organizations must adopt a holistic approach that combines automated security tools with continuous employee training. The most effective PDF security strategies recognize that human behavior is as critical as technological defenses, requiring ongoing education and awareness programs to create a culture of cybersecurity vigilance.
Pro tip: Develop a comprehensive PDF security playbook that includes automated scanning tools, regular vulnerability assessments, and mandatory security awareness training for all employees.
Advanced Solutions for Enterprise PDF Security
Enterprise PDF security demands sophisticated, multi-dimensional approaches that transcend traditional protective measures. Advanced cybersecurity technologies are revolutionizing how organizations defend against increasingly complex digital threats targeting document ecosystems.
Cutting-edge enterprise PDF security solutions incorporate several critical technological innovations:
- Artificial Intelligence Detection: Implementing machine learning algorithms to identify and neutralize potential threats
- Zero Trust Architecture: Enforcing strict authentication for every PDF access attempt
- Blockchain Verification: Ensuring document integrity through immutable transaction records
- Quantum-Resistant Cryptography: Developing encryption methods resilient to advanced computational attacks
- Continuous Threat Monitoring: Real-time scanning and adaptive security controls
NIST cybersecurity frameworks emphasize the importance of integrating advanced technological solutions within comprehensive security strategies. These approaches recognize that PDF security is not a static concept but a dynamic, evolving challenge requiring constant innovation and adaptation.
Successful enterprise PDF security strategies must blend technological sophistication with human-centric approaches, recognizing that technological tools are most effective when complemented by robust organizational policies and continuous employee education.
Here’s a comparison of traditional versus advanced enterprise PDF security solutions:
| Security Approach | Detection Capability | Implementation Complexity |
|---|---|---|
| Traditional Antivirus | Basic known threats only | Low |
| AI-Powered Analysis | Unknown and new patterns | High |
| Manual Encryption | Protects at file level | Medium |
| Zero Trust Architecture | Per-access enforcement | High |
| Blockchain Verification | Tamper-proof authenticity | Very High |
Pro tip: Implement a holistic PDF security strategy that combines advanced AI-driven detection tools, strict access protocols, and mandatory security awareness training to create a comprehensive defense ecosystem.
Strengthen Your PDF Security with Expert Tools and Solutions
Managing PDF security risks like unauthorized access, script injection, and data leakage can feel overwhelming for IT managers aiming to protect sensitive information and maintain compliance. The challenges discussed in “Common PDF Security Risks What IT Managers Must Know” highlight the urgent need for proactive strategies including access control, secure document handling, and vulnerability mitigation.
Discover how Mapsoft’s advanced PDF enhancements and workflow automations can help you secure your documents with trusted solutions tailored to enterprise needs. Our tools empower you to implement encryption, manage metadata, and automate protection processes while ensuring compliance with digital preservation standards.
Take control of your PDF security today by exploring our Digital Preservation category for specialized resources. Get started now with comprehensive solutions designed to optimize your Adobe workflows and protect your organization’s documents at Mapsoft.com. Don’t wait until a vulnerability impacts your business—secure your PDFs with us and stay ahead of evolving threats.
Frequently Asked Questions
What are the common security risks associated with PDF documents?
PDF documents face several security risks, including unauthorized access, malicious code embedding, data leakage, and injection attacks. These vulnerabilities can compromise system integrity and expose sensitive information.
How can organizations prevent PDF security breaches?
Organizations can prevent PDF security breaches by implementing comprehensive security protocols, such as regular vulnerability assessments, strict access controls, and advanced encryption techniques. Additionally, employee training on recognizing threats is crucial.
What types of vulnerabilities are typically found in PDF files?
Common vulnerabilities in PDF files include script injection, use-after-free errors, buffer overflow attacks, privilege escalation, and metadata exposure. Attackers exploit these vulnerabilities to access confidential information and compromise systems.
Why is it important for IT managers to continuously monitor PDF security?
Continuous monitoring of PDF security is vital because the landscape of digital threats is constantly evolving. New vulnerabilities and attack techniques can emerge, making proactive risk management essential for safeguarding sensitive organizational data.
Recommended
- Understanding the Importance of Document Security –
- Cybersecurity Essentials: Empower Your Business Today
- 7 Secure File Sharing Methods Every PDF Workflow Needs –
- The Essential Guide to Handling Confidential Information –
- Sicherheitstraining mit VR umsetzen: Unternehmen optimal schützen – Amlogy AR|VR
- Understanding Why Authenticate Digital Documents for Security



