Cybersecurity sounds technical, but the stakes could not be higher. Cybercrime damages are expected to hit $10.5 trillion a year by 2025, making digital protection a major business concern. It might seem like high-tech software is the only answer, but the real key is understanding the basic principles that shape every strong defense.
Table of Contents
- What Are Cybersecurity Essentials And Why They Matter?
- Key Concepts In Cybersecurity: Threats And Vulnerabilities
- The Role Of Cybersecurity In Business Operations
- Practical Applications Of Cybersecurity Essentials
- Building A Cybersecurity Culture In Your Organization
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement proactive cybersecurity strategies. | Continuous updates to defenses and employee training reduce risks significantly. |
| Educate employees on cybersecurity protocols. | Effective training transforms staff into active defenders against digital threats. |
| Recognize and address digital vulnerabilities. | Regular assessments of weak points help organizations mitigate potential attacks. |
| Integrate cybersecurity into business operations. | Viewing cybersecurity as a core function enhances organizational resilience and financial performance. |
| Foster a cybersecurity culture organization-wide. | Leadership commitment and continuous learning create a shared responsibility for digital safety. |
What are Cybersecurity Essentials and Why They Matter?
Cybersecurity essentials represent the fundamental strategies and practices organizations implement to protect their digital assets, networks, and sensitive information from unauthorized access, attacks, and potential breaches. Understanding these core principles is crucial for businesses operating in an increasingly complex digital landscape.
The Core Definition of Cybersecurity
At its foundation, cybersecurity is a comprehensive approach to safeguarding computer systems, networks, programs, and data from digital threats. According to the National Institute of Standards and Technology (NIST), cybersecurity involves implementing protective measures that prevent, detect, and respond to potential security incidents.
Key components of cybersecurity essentials include:
- Network Protection: Securing communication channels and preventing unauthorized access
- Data Encryption: Transforming sensitive information into unreadable code
- Access Control: Managing user permissions and authentication processes
- Threat Detection: Monitoring systems for potential security vulnerabilities
Strategic Importance for Business Survival
Research from Cybersecurity Ventures reveals that global cybercrime damages are projected to reach $10.5 trillion annually by 2025. This staggering statistic underscores why cybersecurity is no longer optional but a critical business imperative.
Businesses face significant risks without robust cybersecurity measures. Potential consequences of inadequate protection include financial losses, reputational damage, legal liabilities, and potential operational disruptions.
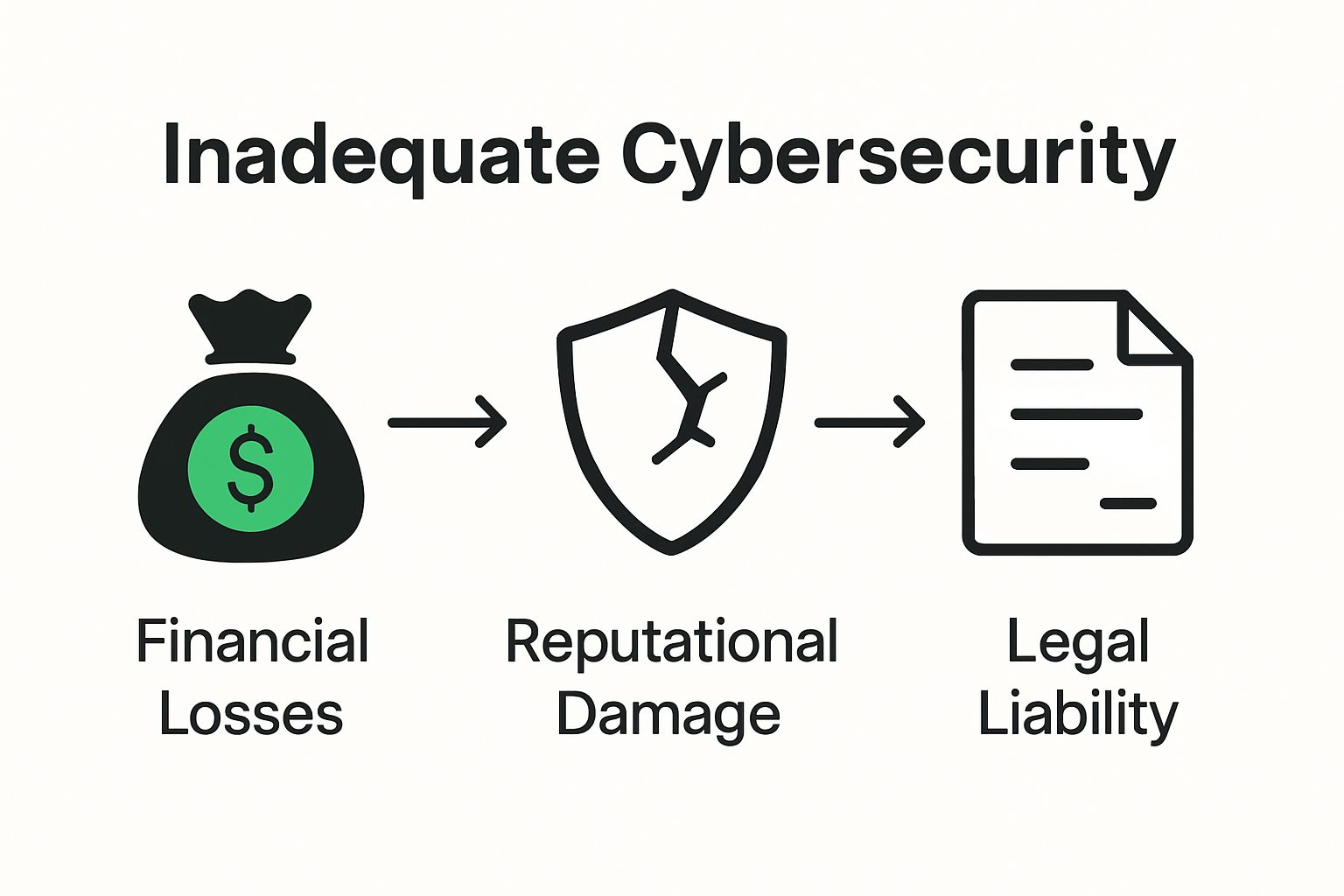 Cybercriminals continuously evolve their tactics, targeting vulnerabilities in organizational digital infrastructure.
Cybercriminals continuously evolve their tactics, targeting vulnerabilities in organizational digital infrastructure.
The most successful cybersecurity strategies adopt a proactive rather than reactive approach. This means continuously updating defense mechanisms, training employees, and maintaining a comprehensive understanding of emerging digital threats. By treating cybersecurity as an ongoing process rather than a one-time implementation, organizations can significantly reduce their risk exposure and maintain operational resilience in an unpredictable digital environment.
Key Concepts in Cybersecurity: Threats and Vulnerabilities
Understanding the landscape of cybersecurity requires a deep comprehension of the various threats and vulnerabilities that organizations face in their digital ecosystems. These complex interactions between potential attackers and system weaknesses form the core challenge of modern digital defense strategies.
To clarify the different types of cybersecurity threats organizations may face, the following table summarizes each threat category and its main characteristics.
| Threat Type | Description |
|---|---|
| Malware | Software designed to damage or gain unauthorized access |
| Phishing | Deceptive attacks to trick users into revealing information |
| Ransomware | Encrypts data and demands payment for restoration |
| Advanced Persistent Threats | Sophisticated, long-term attacks targeting specific organizations |
Types of Cybersecurity Threats
According to the SANS Institute, cybersecurity threats can be categorized into several distinct types that pose significant risks to organizational infrastructure. Malicious actors leverage multiple approaches to exploit system vulnerabilities and compromise digital assets.
Key cybersecurity threat categories include:
- Malware: Software designed to damage or gain unauthorized access to computer systems
- Phishing: Social engineering attacks attempting to deceive users into revealing sensitive information
- Ransomware: Malicious software that encrypts system data and demands payment for restoration
- Advanced Persistent Threats (APTs): Sophisticated, prolonged attacks targeting specific organizations
Understanding Digital Vulnerabilities
Research from IBM Security highlights that human error accounts for approximately 95% of cybersecurity vulnerabilities. These weaknesses can emerge from multiple sources, ranging from outdated software systems to inadequate employee training and misconfigured network settings.
Vulnerabilities represent potential entry points that cybercriminals can exploit. Critical vulnerability areas often include unpatched software, weak authentication mechanisms, misconfigured cloud services, and insufficient network segmentation. Organizations must continuously assess and address these potential weak points to maintain robust defensive capabilities.
The evolving nature of cyber threats demands a proactive and adaptive approach to cybersecurity. By understanding the intricate relationship between potential threats and system vulnerabilities, businesses can develop more comprehensive and effective defense strategies. Continuous monitoring, regular security assessments, and a culture of digital awareness are essential in mitigating risks and protecting organizational digital assets from sophisticated cyber attacks.
The Role of Cybersecurity in Business Operations
Cybersecurity has transformed from a technical afterthought to a critical strategic component of modern business operations. Organizations now recognize that digital protection is not merely an IT function but a fundamental aspect of sustainable business strategy that directly impacts organizational resilience, reputation, and financial performance.
Protecting Organizational Assets
According to the Small Business Administration, cybersecurity plays a crucial role in safeguarding an organization’s most valuable digital assets. Comprehensive protection extends beyond technical infrastructure and encompasses protecting intellectual property, customer data, financial records, and operational information.
Key organizational assets requiring cybersecurity protection include:
- Intellectual Property: Proprietary designs, research, and innovative strategies
- Customer Data: Personal information, transaction records, and contact details
- Financial Information: Banking details, transaction logs, and financial forecasts
- Operational Systems: Communication networks, cloud storage, and enterprise software
Business Continuity and Risk Management
Research from Gartner indicates that cybersecurity breaches can cause significant operational disruptions, with potential financial losses exceeding millions of dollars. Effective cybersecurity strategies are no longer optional but essential for maintaining business continuity and managing digital risk.
Strategic cybersecurity implementation involves developing robust incident response plans, conducting regular vulnerability assessments, and creating adaptive security frameworks that can quickly respond to emerging digital threats. By integrating cybersecurity into core business operations, organizations can minimize potential disruptions, protect their reputation, and maintain customer trust.

Modern businesses must view cybersecurity as a dynamic, ongoing process that requires continuous investment, employee education, and technological adaptation. The most successful organizations recognize that cybersecurity is not just about preventing attacks but about creating a resilient digital ecosystem that can withstand and quickly recover from potential security incidents.
To help distinguish the key organizational assets requiring protection, the following table outlines examples with brief explanations.
| Asset | Examples | Protection Focus |
|---|---|---|
| Intellectual Property | Proprietary designs, research, strategies | Prevent theft and unauthorized access |
| Customer Data | Personal information, transaction records | Ensure privacy, prevent breaches |
| Financial Information | Banking details, transaction logs, forecasts | Safeguard against fraud and loss |
| Operational Systems | Networks, cloud storage, enterprise software | Maintain continuity and reliability |
Practical Applications of Cybersecurity Essentials
Implementing cybersecurity essentials requires a strategic and holistic approach that goes beyond theoretical knowledge. Organizations must translate conceptual understanding into actionable, real-world defense mechanisms that protect their digital infrastructure and sensitive information.
Employee Training and Awareness Programs
According to the National Cyber Security Centre, human error remains one of the most significant vulnerabilities in cybersecurity. Effective cybersecurity begins with comprehensive employee education that transforms staff from potential security risks into active defenders of organizational digital assets.
Key components of robust cybersecurity training include:
- Phishing Recognition: Teaching employees to identify suspicious emails and potential social engineering attempts
- Password Management: Implementing strong password creation and management protocols
- Device Security: Understanding risks associated with personal and work devices
- Incident Reporting: Establishing clear procedures for reporting potential security threats
Technology and Infrastructure Protection
Research from Forrester demonstrates that organizations must implement multilayered security approaches that combine technological solutions with strategic planning. Technical cybersecurity applications involve deploying advanced protective technologies and creating resilient digital environments.
Critical technological protections include network segmentation, multi-factor authentication, encryption protocols, and continuous monitoring systems. Learn more about document security strategies to enhance your organizational protection framework.
Practical cybersecurity is an adaptive process that requires ongoing assessment, improvement, and alignment with emerging technological landscapes. Successful implementations recognize that cybersecurity is not a static solution but a dynamic strategy that evolves alongside digital threats. Organizations must develop flexible, comprehensive approaches that integrate technological tools, human expertise, and proactive risk management techniques.
Building a Cybersecurity Culture in Your Organization
Creating a robust cybersecurity culture transcends technical implementations and requires a fundamental shift in organizational mindset, behavior, and collective responsibility. Organizations must transform cybersecurity from a technical department function into a shared commitment embraced by every employee at every organizational level.
Leadership and Strategic Commitment
According to Deloitte’s Cyber Risk Management research, successful cybersecurity culture begins with visible and consistent leadership engagement. Top management must demonstrate an unwavering commitment to digital security by allocating resources, setting clear expectations, and modeling secure behaviors throughout the organization.
Critical leadership responsibilities in building cybersecurity culture include:
- Resource Allocation: Investing in training, technologies, and security infrastructure
- Policy Development: Creating clear, comprehensive cybersecurity guidelines
- Regular Communication: Consistently reinforcing the importance of digital security
- Performance Integration: Incorporating security metrics into organizational evaluations
Continuous Learning and Empowerment
Research from MIT Sloan Management Review emphasizes that cybersecurity is fundamentally about empowering employees to become active participants in organizational defense. Effective cybersecurity cultures transform employees from potential vulnerabilities into informed, vigilant protectors.
This approach requires developing ongoing educational programs that provide practical skills, create engaging learning experiences, and foster a proactive security mindset. Organizations must move beyond mandatory annual training sessions and create dynamic, interactive learning environments that help employees understand their critical role in maintaining digital safety.
Building a cybersecurity culture is an evolutionary process that requires persistent effort, strategic communication, and a genuine commitment to creating a security-first organizational environment. By integrating cybersecurity principles into daily operations, reward systems, and organizational values, businesses can develop a resilient, adaptive approach to digital protection that goes far beyond traditional technical solutions.
Transform Cybersecurity Awareness into Practical PDF Protection for Your Business
You have seen how lacking cybersecurity essentials can open your organization to human error, data breaches, and operational disruption. When your business relies on large volumes of digital documents or PDF workflows, the risk of compromised files or unauthorized access is even higher. The article highlighted the urgent need for robust document protection, threat detection, and consistent employee training. Now is the time to turn that knowledge into action.
Secure your critical PDF assets from malicious attacks and compliance risks without sacrificing productivity. Mapsoft.com has a proven record of helping businesses like yours strengthen document protection with advanced PDF security, batch automation, and seamless Adobe integration. Take your cybersecurity strategy further. Explore Mapsoft PDF Hub for large-scale PDF processing, or get tailored advice and see how our consultancy services support your digital transformation. Fortify your organization’s documents now and build a resilient cybersecurity culture from the inside out.
Frequently Asked Questions
What are the core components of cybersecurity essentials for businesses?
Cybersecurity essentials include network protection, data encryption, access control, and threat detection. Start by implementing these four key strategies to establish a strong foundation for your organization’s digital security.
How can I train my employees on cybersecurity awareness?
To effectively train employees, develop a structured program that covers topics like phishing recognition and password management. Conduct regular training sessions at least quarterly to enhance awareness and reduce vulnerabilities by about 30%.
What steps can I take to assess my organization’s cybersecurity vulnerabilities?
Begin by conducting a comprehensive security audit to identify potential weaknesses in your systems. Focus on areas like outdated software and misconfigured settings, and complete this assessment within 3 months to develop a timely risk management plan.
How can I create an incident response plan for cybersecurity issues?
Create an incident response plan by defining roles and establishing clear procedures for responding to security threats. Ensure that this plan is documented and communicated to all employees, reviewing and updating it every six months to keep it relevant.
Why is employee education important for effective cybersecurity?
Employee education is crucial because human error accounts for a significant percentage of cybersecurity breaches. Invest in ongoing training and interactive learning experiences to empower employees to recognize and mitigate potential security threats, aiming to reduce errors by up to 50% over 12 months.
How can I integrate cybersecurity into my overall business strategy?
Integrate cybersecurity into your business strategy by involving top management in establishing policies and allocating resources for security measures. Ensure cybersecurity is a regular topic in strategic discussions to align it with your business goals and enhance overall resilience.
Recommended
- Understanding the Importance of Document Security –
- Fierce Strategies for Disaster Planning for Businesses
- Achieving Success by Balancing Security and Usability
- Master Secure Document Sharing for Business Success –
Understanding cybersecurity essentials is vital for any organization aiming to protect its digital environment. Cybersecurity essentials must be at the forefront of all business strategies.



