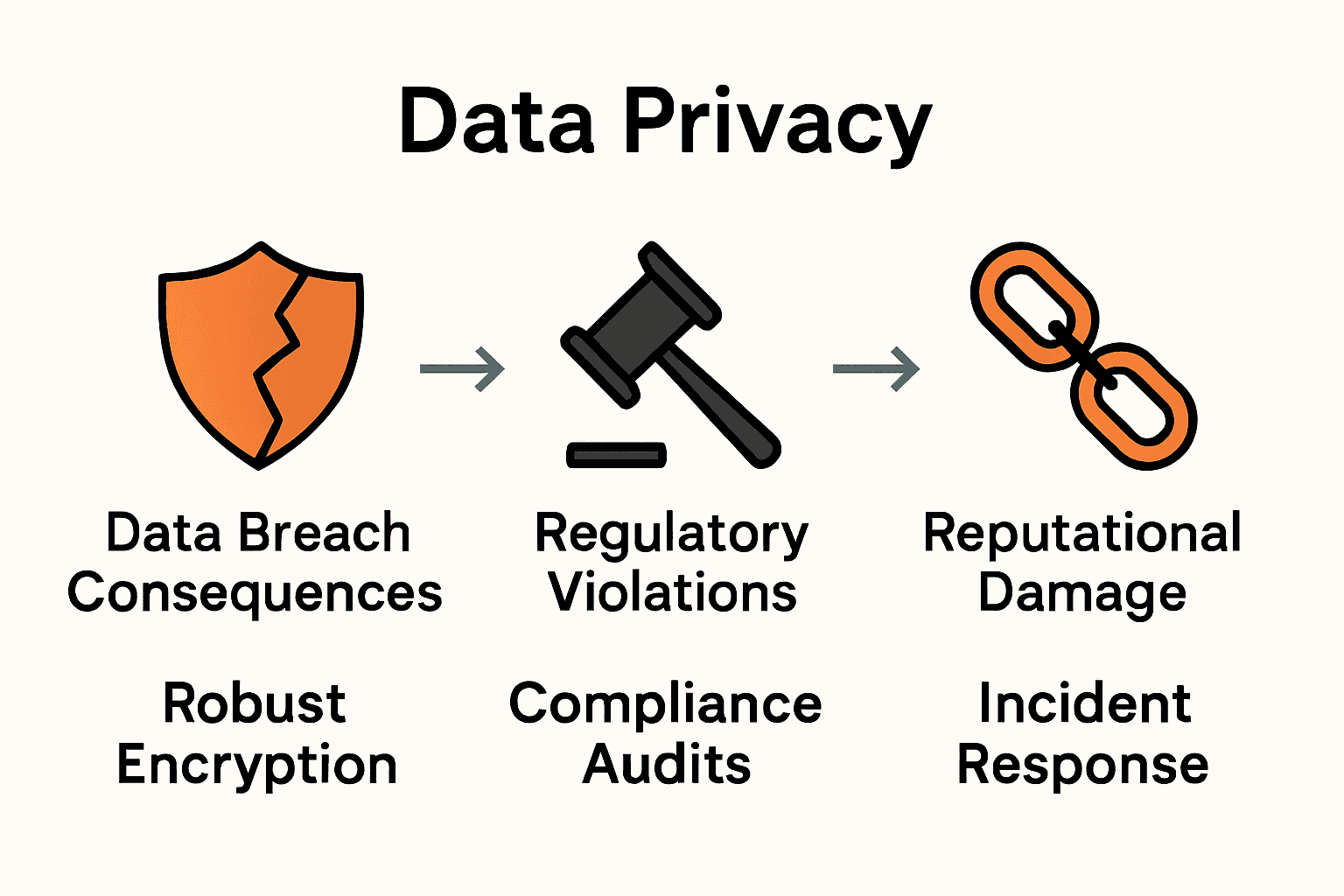
More than 90 percent of enterprises face data privacy concerns that can lead to severe financial and reputational loss. As digital information grows, protecting sensitive company data is now a top priority for every organization. Understanding the fundamentals of enterprise data privacy gives teams a solid foundation to defend valuable assets, stay compliant with powerful laws, and minimize costly mistakes.
Table of Contents
- Enterprise Data Privacy Fundamentals Explained
- Types of Data and Privacy Classifications
- Legal Frameworks and Compliance Standards
- Enterprise Data Handling and Protection Practices
- Risks, Liabilities, and Compliance Pitfalls
Key Takeaways
| Point | Details |
|---|---|
| Comprehensive Data Privacy Framework | Successful enterprise data privacy requires a layered strategy combining regulatory compliance, technical safeguards, and organizational policies. |
| Data Classification is Essential | Understanding the sensitivity of data through classification is crucial for implementing appropriate protection measures and resource allocation. |
| Ongoing Compliance and Risk Management | Compliance is an ongoing process that necessitates continuous monitoring and adaptation to evolving regulatory landscapes to mitigate risks. |
| Holistic Protection Practices | Effective data protection involves a systematic approach including labeling, access control, encryption, and regular audits to safeguard sensitive information. |
Enterprise Data Privacy Fundamentals Explained
Enterprise data privacy is a critical framework that protects organizational information assets from unauthorized access, misuse, or exposure. According to Big Data Framework, comprehensive data privacy strategies encompass multiple layers of protection, including regulatory compliance, technical safeguards, and organizational policies.
At its core, enterprise data privacy involves classifying and protecting different information types based on their sensitivity level. UAB highlights three primary data classification levels that organizations must understand and implement:
- Public Data: Information that can be freely shared without risk
- Sensitive Data: Information requiring controlled access
- Restricted Data: Highly confidential information with strict handling requirements
Successful data privacy implementation requires a holistic approach that integrates technological solutions, employee training, and robust governance frameworks. Organizations must develop comprehensive strategies that address:
- Risk assessment and identification of potential vulnerabilities
- Implementation of encryption and access control mechanisms
- Regular security audits and monitoring
- Clear incident response protocols
- Ongoing employee education and awareness programs
By understanding and proactively managing data privacy fundamentals, enterprises can protect their most valuable digital assets while maintaining compliance with evolving regulatory standards.

Types of Data and Privacy Classifications
Understanding data classification is fundamental to creating robust privacy strategies in enterprise environments. Rice University provides a comprehensive framework that categorizes data into three critical risk levels, each demanding unique protection protocols and security approaches.
The primary data classification levels typically include:
- General/Public Data (Low Risk): Information that can be freely shared without potential organizational harm
- Sensitive Data (Moderate Risk): Information requiring controlled access and intermediate protection measures
- Confidential and Regulated Data (High Risk): Highly sensitive information with strict security requirements
University of Colorado expands on these classifications, emphasizing that each data type requires tailored security mechanisms. High-risk data demands the most stringent protection, including:
- Advanced encryption protocols
- Multi-factor authentication
- Restricted access controls
- Comprehensive audit trails
- Regular security assessments
Effective data classification enables organizations to allocate resources strategically, ensuring that the most critical information receives the highest level of protection while maintaining operational efficiency and regulatory compliance.
Legal Frameworks and Compliance Standards
Enterprise data privacy is increasingly governed by complex legal frameworks that demand rigorous compliance across multiple regulatory domains. North Dakota Information Technology highlights the critical importance of understanding and implementing comprehensive data protection strategies that align with national and industry-specific regulations.
Key legal frameworks organizations must navigate include:
- GDPR: European Union’s comprehensive data protection regulation
- HIPAA: Healthcare information privacy standards
- PCI-DSS: Payment card industry data security requirements
- CCPA: California consumer privacy regulations
- NIST: National cybersecurity and privacy guidelines
University of Alabama at Birmingham emphasizes that compliance is not a one-time achievement but an ongoing process requiring continuous monitoring, assessment, and adaptation. Organizations must develop robust mechanisms to:
- Continuously track regulatory changes
- Implement comprehensive data mapping
- Conduct regular privacy impact assessments
- Maintain detailed documentation of data handling processes
- Train employees on current compliance requirements
Successful legal compliance demands a proactive, holistic approach that integrates technical safeguards, organizational policies, and a deep understanding of evolving regulatory landscapes.
Enterprise Data Handling and Protection Practices
Effective enterprise data protection requires a systematic approach that goes beyond basic security measures. Vanderbilt University emphasizes the critical importance of comprehensive data handling practices that adapt to varying levels of information sensitivity.
Key protection strategies include:
- Data Labeling: Clearly identifying the classification and sensitivity of each data asset
- Access Control: Implementing granular permissions based on user roles and data classification
- Encryption: Protecting data both at rest and in transit
- Secure Storage: Utilizing advanced storage solutions with built-in security features
- Regular Auditing: Continuously monitoring and reviewing data access and usage
Towson University recommends a multi-layered approach to data protection that encompasses technological, procedural, and human elements. Organizations must develop robust mechanisms to:
- Create comprehensive data handling policies
- Implement advanced authentication mechanisms
- Develop clear incident response protocols
- Conduct regular security awareness training
- Establish continuous monitoring systems
Successful data protection is not about implementing a single solution, but creating a holistic ecosystem that adapts to evolving technological and regulatory landscapes while maintaining the delicate balance between accessibility and security.
Risks, Liabilities, and Compliance Pitfalls
Enterprise data management involves navigating a complex landscape of potential risks and legal vulnerabilities. Lewis-Clark State College emphasizes that improper data handling can expose organizations to significant financial and reputational damages across multiple dimensions.
Primary compliance risks include:
- Data Breach Consequences: Potential multi-million dollar penalties
- Regulatory Violations: Fines and legal sanctions
- Reputational Damage: Loss of customer trust and market credibility
- Operational Disruptions: Potential business continuity challenges
- Intellectual Property Exposure: Risks of sensitive information leakage
University of Alabama at Birmingham recommends organizations implement comprehensive risk mitigation strategies through:
- Proactive risk assessment protocols
- Regular compliance audits
- Robust incident response planning
- Continuous employee training programs
- Advanced technological safeguards
Successful risk management requires a dynamic, holistic approach that anticipates potential vulnerabilities, implements multilayered protection mechanisms, and maintains flexibility in responding to emerging technological and regulatory challenges.
Strengthen Your Enterprise Data Privacy with Smarter PDF and Workflow Solutions
Managing data privacy challenges like classification, encryption, and compliance requires more than just policies. This article highlights critical pain points such as controlling access to sensitive information, ensuring consistent data handling practices, and meeting evolving regulatory demands. At Mapsoft, we understand these needs and provide specialized tools designed to safeguard your enterprise documents while optimizing workflow efficiency.
Secure your organization’s most valuable digital assets by leveraging Mapsoft’s advanced Adobe Acrobat® plugins and the powerful Mapsoft PDF Hub platform. Easily automate document processes like redaction, password protection, and metadata management to enforce privacy controls effortlessly. Act now to transform your PDF workflows into a compliant, streamlined operation. Visit Mapsoft.com to explore customized solutions tailored for enterprises aiming to excel in data privacy and protection.
Frequently Asked Questions
What are the key components of enterprise data privacy?
Enterprise data privacy involves regulatory compliance, technical safeguards, and organizational policies. It includes risk assessment, encryption, access control, and employee education to protect sensitive information.
How are data types classified in enterprise data privacy?
Data types are typically classified into three categories: Public Data (low risk), Sensitive Data (moderate risk), and Restricted Data (high risk). Each classification requires different protection measures and access controls.
What legal frameworks govern enterprise data privacy?
Key legal frameworks include GDPR, HIPAA, PCI-DSS, CCPA, and NIST. Organizations must understand and comply with these regulations to avoid penalties and ensure data protection.
What are common risks and liabilities associated with data privacy?
Common risks include data breaches, regulatory violations, reputational damage, operational disruptions, and exposure of intellectual property. Implementing robust risk management strategies helps mitigate these threats.